
Solutions
Network and Vulnerability Management
|
|||||||||
FREEWARE version available - See how vulnerable your organization is to such breaches:
In freeware mode, functionality is limited to monitoring only but there is no limit on the number of agents that can be deployed, so administrators can immediately see what is happening on monitored machines.
In freeware mode, functionality is limited to monitoring only but there is no limit on the number of agents that can be deployed, so administrators can immediately see what is happening on monitored machines.
NEW! Encryption for removable devices – even while on the road
Blocking access to USB storage devices ensures that no data is stolen from your organization; however, there are times when you need to permit your users to utilize portable storage devices.
Blocking access to USB storage devices ensures that no data is stolen from your organization; however, there are times when you need to permit your users to utilize portable storage devices.
How it works
To control access, GFI EndPointSecurity installs a small footprint agent on your user's machine. This agent is only 1.2 MB in size, meaning your user will never know it is there.
To control access, GFI EndPointSecurity installs a small footprint agent on your user's machine. This agent is only 1.2 MB in size, meaning your user will never know it is there.
Manage user access and protect your network from portable devices
Using GFI EndPointSecurity you can centrally disable access to any portable device, preventing both data theft and the introduction of data or software that could be harmful to your network.
Using GFI EndPointSecurity you can centrally disable access to any portable device, preventing both data theft and the introduction of data or software that could be harmful to your network.
Centralized monitoring
GFI EndPointSecurity incorporates a dedicated node making it possible for administrators to view all computers on a network from a single location.
GFI EndPointSecurity incorporates a dedicated node making it possible for administrators to view all computers on a network from a single location.
Computer auto-discovery and automatic protection
GFI EndPointSecurity can monitor the network, detect new computers that are connected onto the network, notify the administrator, and perform various tasks as configured by the administrator.
GFI EndPointSecurity can monitor the network, detect new computers that are connected onto the network, notify the administrator, and perform various tasks as configured by the administrator.
Supports Windows 7 and BitLockerTo Go
Windows 7’s “BitLocker To Go” is designed to encrypt data on removable devices.
Windows 7’s “BitLocker To Go” is designed to encrypt data on removable devices.
Get detailed reports on device usage with GFI EndPointSecurity ReportPack™ add-on
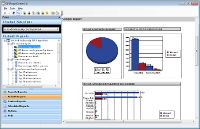 The GFI EndPointSecurity ReportPack is a powerful reporting package that adds on for free to GFI EndPointSecurity.
The GFI EndPointSecurity ReportPack is a powerful reporting package that adds on for free to GFI EndPointSecurity.

Windows 7 support for tamper-proof agent
The agent used to control machines has a number of security elements applied to render it tamper-proof.
The agent used to control machines has a number of security elements applied to render it tamper-proof.
NEW! Product update mechanism
GFI EndPointSecurity auto-updates via GFI’s servers – this functionality allows GFI to roll out fixes immediately without troubling the administrator to download and install upgrades.
GFI EndPointSecurity auto-updates via GFI’s servers – this functionality allows GFI to roll out fixes immediately without troubling the administrator to download and install upgrades.
NEW! Database maintenance - rollover functionality
GFI EndPointSecurity removes another administrative headache – database size limits. Based on the database size limit (4 GB) imposed by SQL Server Express, the product can automatically roll over and start report-logging in a new database once the original one is full.
GFI EndPointSecurity removes another administrative headache – database size limits. Based on the database size limit (4 GB) imposed by SQL Server Express, the product can automatically roll over and start report-logging in a new database once the original one is full.
Log the activity of portable device access to your network
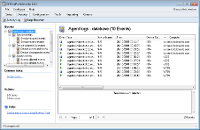 USB sticks present a significant threat to your business environment. They are small, easily hidden and can store up to 16 GB of data.
USB sticks present a significant threat to your business environment. They are small, easily hidden and can store up to 16 GB of data.

Easily configure group-based protection control via active directory
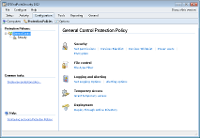 You can categorize computers into protection groups. For each group you may specify the level of protection and portable device access to allow.
You can categorize computers into protection groups. For each group you may specify the level of protection and portable device access to allow.

Advanced granular access control via whitelists and blacklists
GFI EndPointSecurity enables you to allow or deny access to a range of device classes, as well as to block files transferred by file extension, by physical port and by device ID (the factory ID that identifies each device).
GFI EndPointSecurity enables you to allow or deny access to a range of device classes, as well as to block files transferred by file extension, by physical port and by device ID (the factory ID that identifies each device).
Real-time status monitoring and alerts
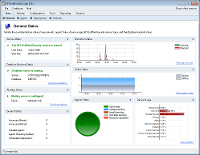 GFI EndPointSecurity provides real-time status monitoring through its user interface.
GFI EndPointSecurity provides real-time status monitoring through its user interface.

Easy unattended agent deployment
GFI EndPointSecurity provides administrators with the ability to automatically schedule agent deployment after a policy or configuration change.
GFI EndPointSecurity provides administrators with the ability to automatically schedule agent deployment after a policy or configuration change.
Permit temporary device access
Temporary access can be granted to users for a device (or group of devices) on a particular computer for a particular timeframe.
Temporary access can be granted to users for a device (or group of devices) on a particular computer for a particular timeframe.
Policy creation wizard
To facilitate the creation of security policies, GFI EndPointSecurity includes a wizard to create security policies. Administrators can also create new policies based on existing ones.
To facilitate the creation of security policies, GFI EndPointSecurity includes a wizard to create security policies. Administrators can also create new policies based on existing ones.
Daily/weekly digest
An email notification containing activity statistics can be sent on a daily or weekly basis, enabling the recipient to have an overview of, for example, how many files were copied to and from devices, how many may potentially carry malware, etc.
An email notification containing activity statistics can be sent on a daily or weekly basis, enabling the recipient to have an overview of, for example, how many files were copied to and from devices, how many may potentially carry malware, etc.
Other features:
- Ability to group computers, e.g., by department, by domain, etc.
- Scan and detect a list of devices that have been used or are currently in use
- Password protected agents to avoid tampering
- Set up custom popup messages for users when they are blocked from using a device
- Browse user activity and device usage logs through a backend database
- Maintenance function that allows you to delete information that is older than a certain number of days
- Support for operating systems in any Unicode compliant language
please contact our Sales Representative at 2556 2162, or email at sales@ppn.com.hk.
Copyright © 2021 Pacific Professional Network. All rights reserved.


